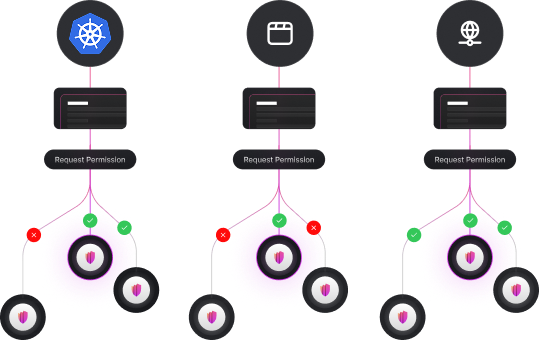
Zone
Create and configure Zero Trust Zones.

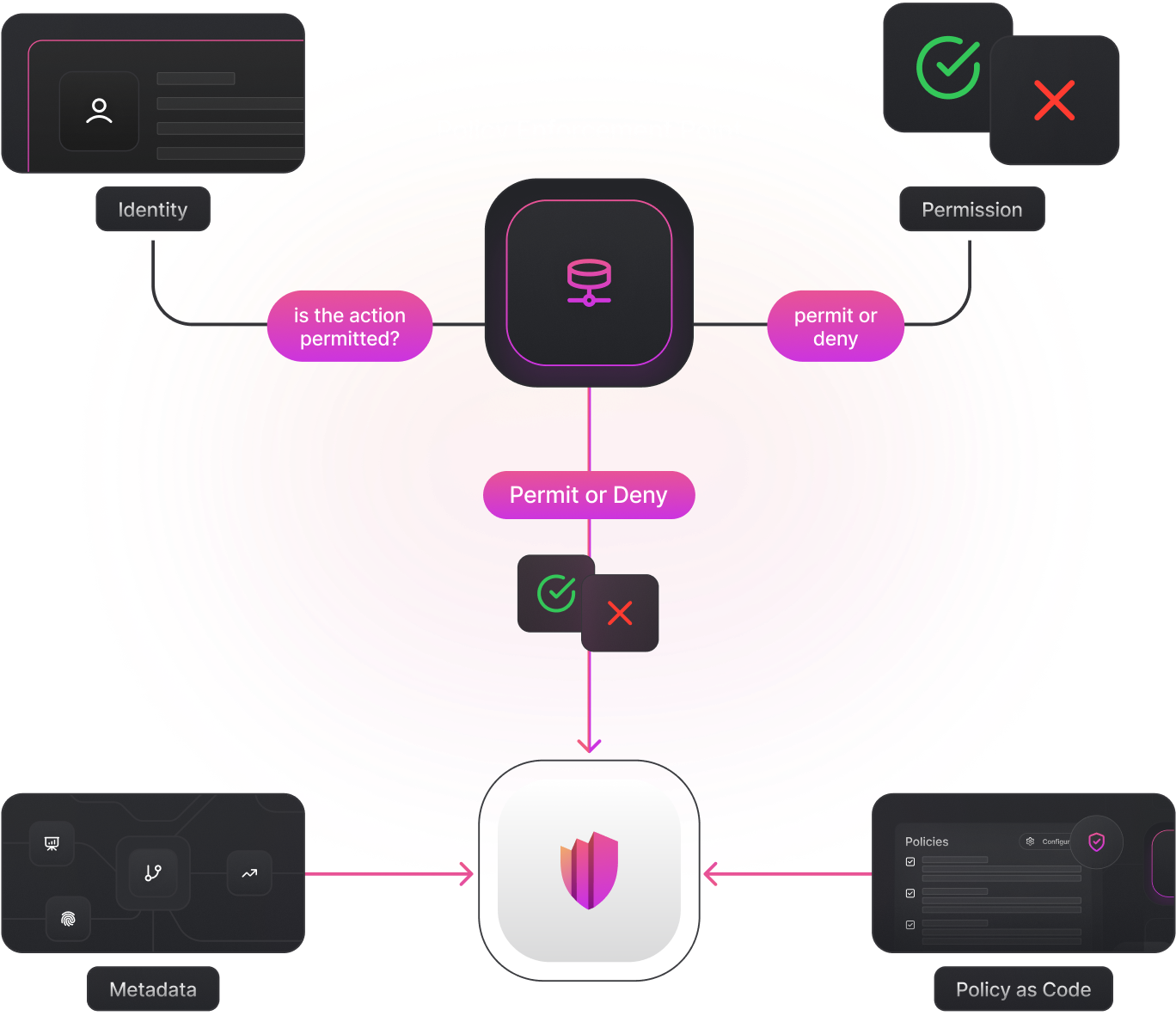
Secure your apps with Zero Trust authorization in minutes.
Get Started


Run your own AuthZServer. Define your trust zones and policies, and finally enforce authorization with zero coupling.

Create and configure Zero Trust Zones.

Support human and non-human identities.
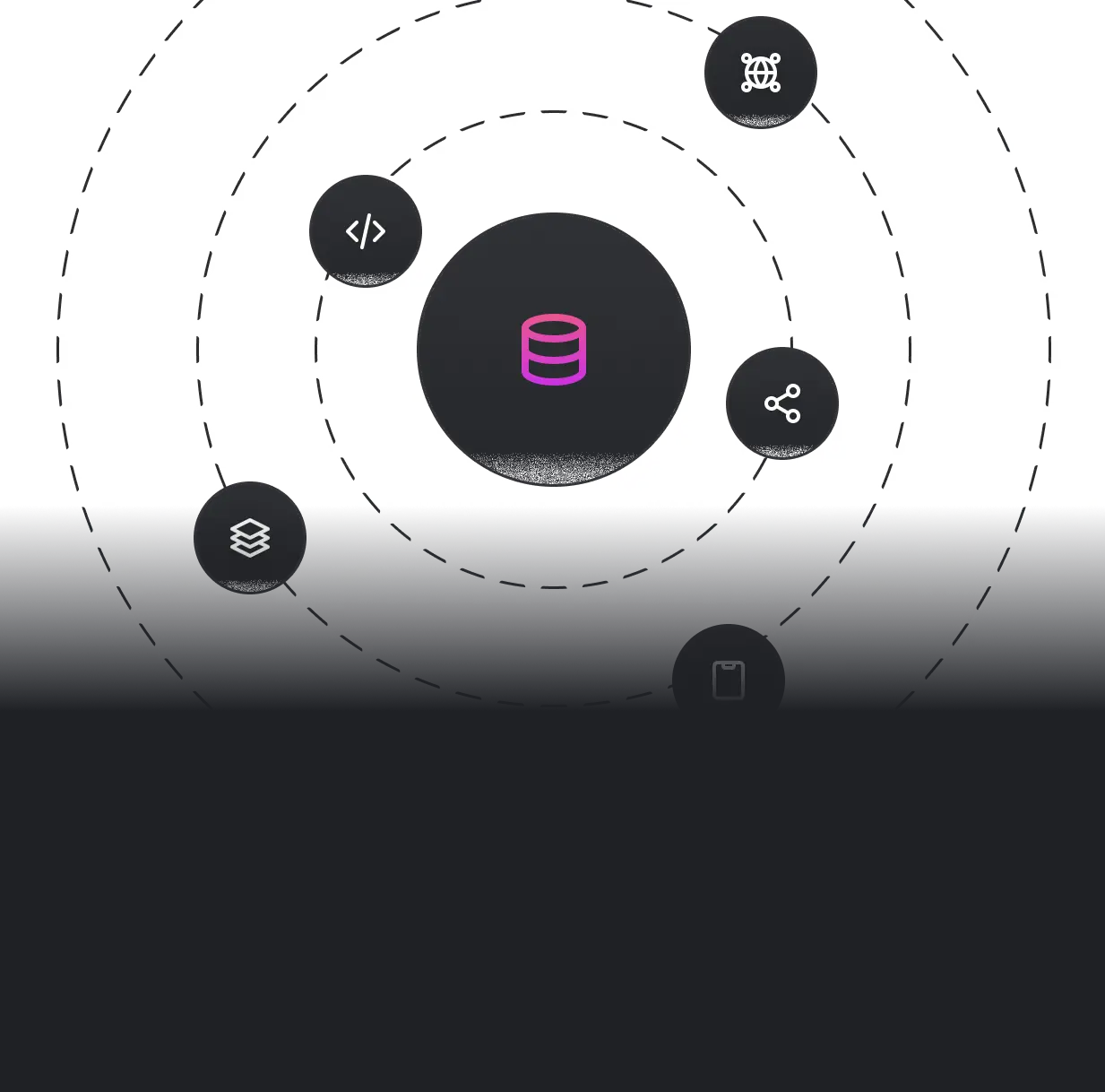
Create Ledgers and configure their Manifest.
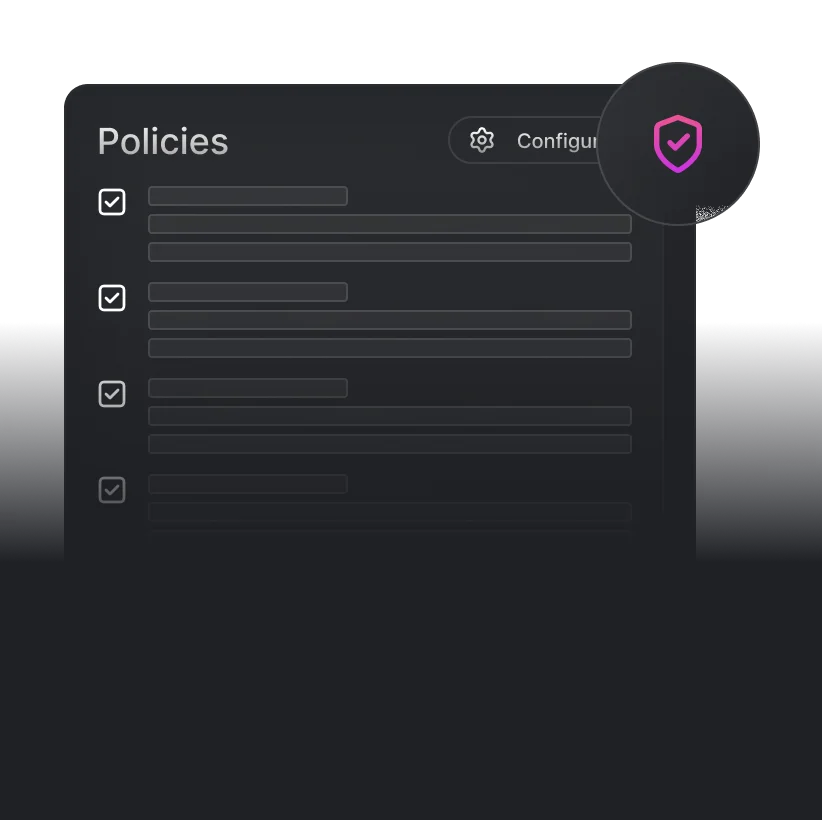
Define policies to control what is permitted or forbidden.
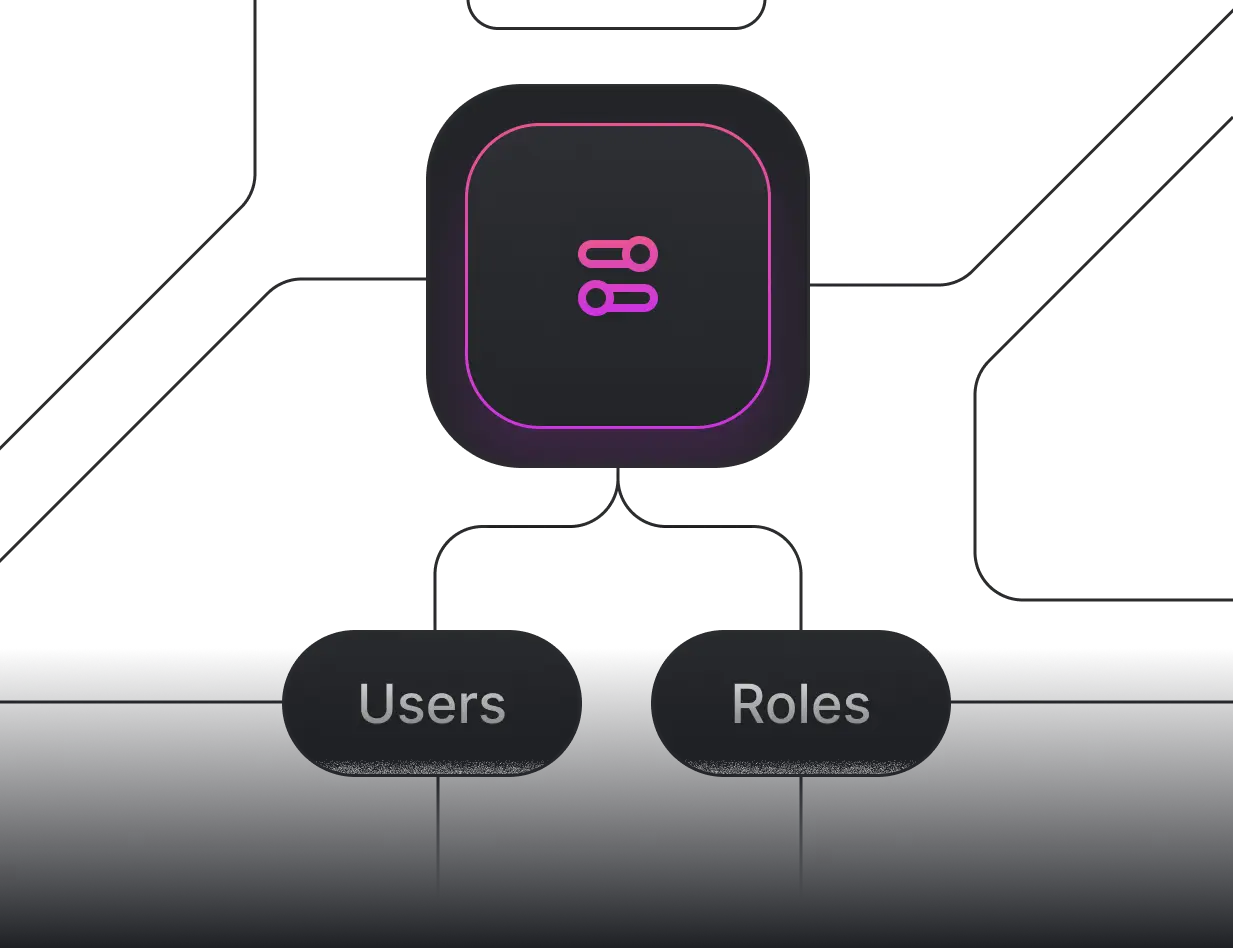
Organize policies using Scopes.
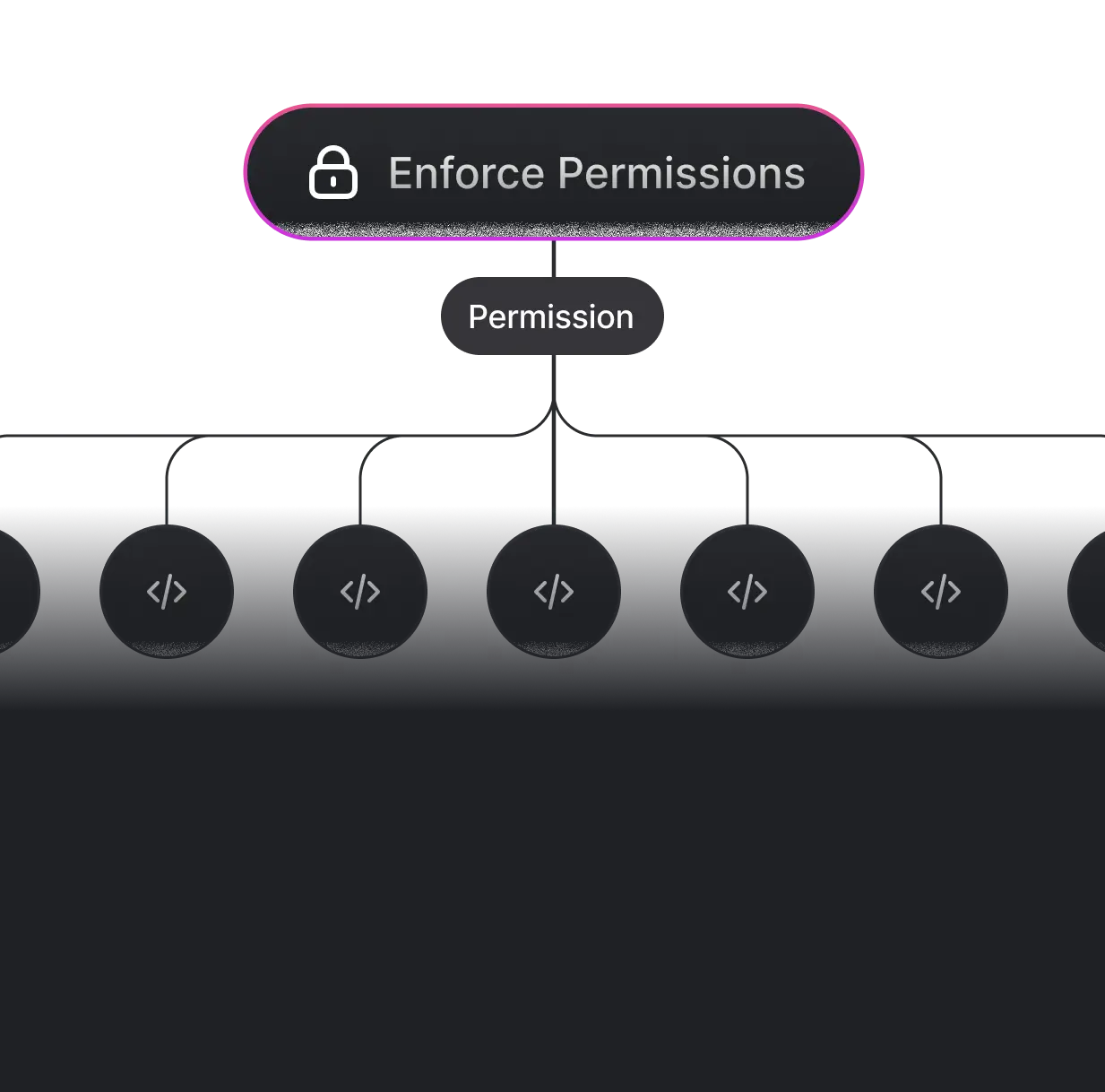
Enforce the permissions in the application using available SDKs.
In Permguard, policies are versioned, immutable, and traceable, just like code in Git. But they’re not just for developers: they’re designed for operational governance and can evolve safely over time. Deploy changes via CI/CD pipelines or manage them directly in production through the admin panel, always with correctness, compliance, and auditability in mind.
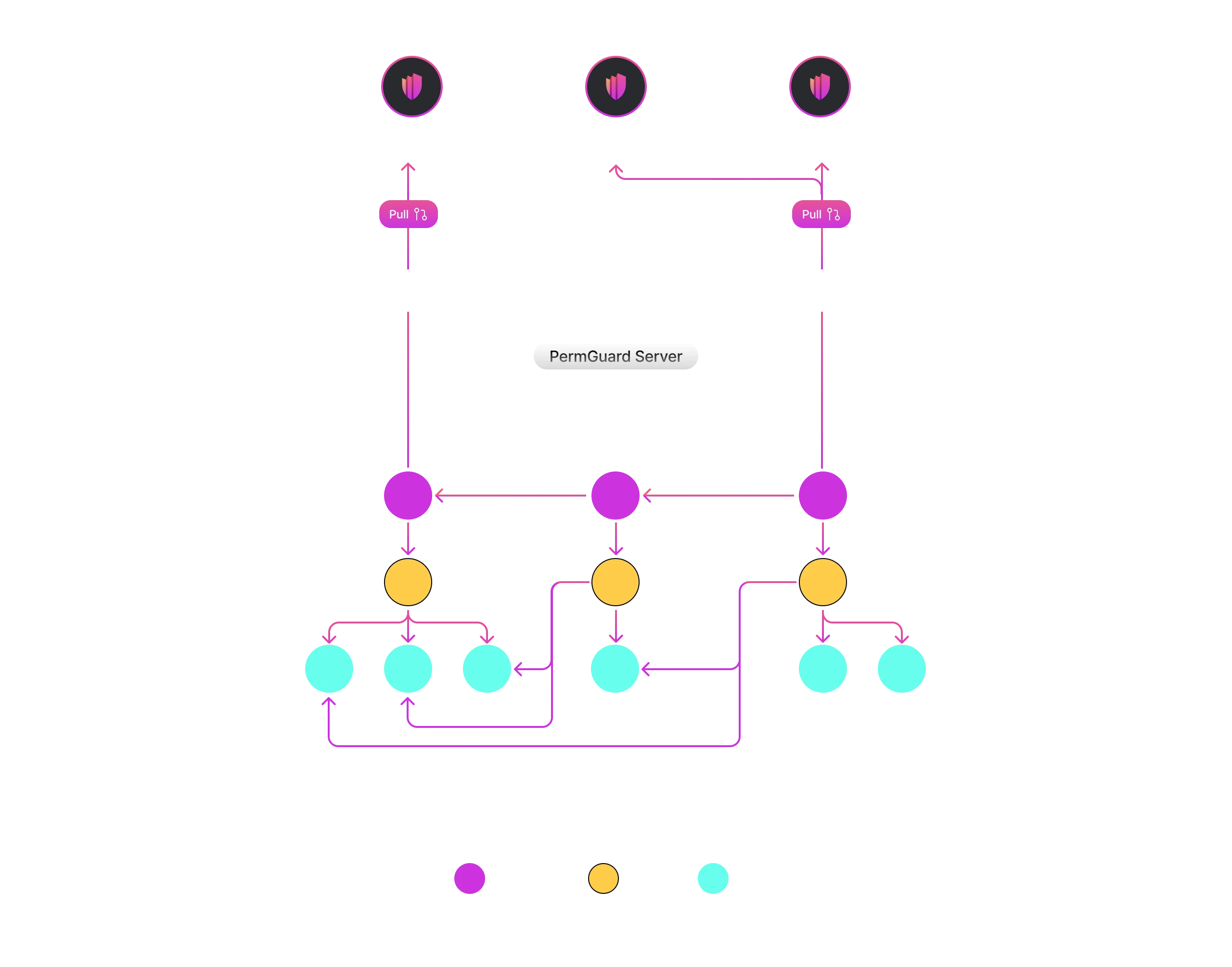
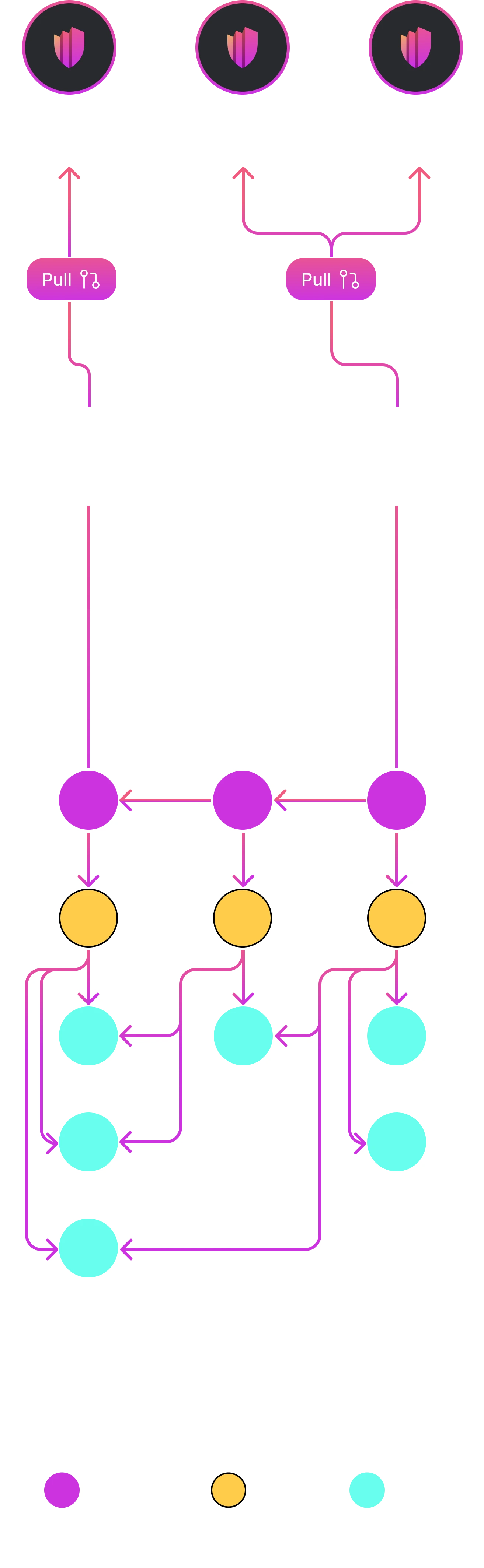
Deploy your AuthZServer and start managing your Trust Zones, Ledgers, and Policies. Finally, integrate the SDK to begin enforcing authorization in your applications.
Step: 1
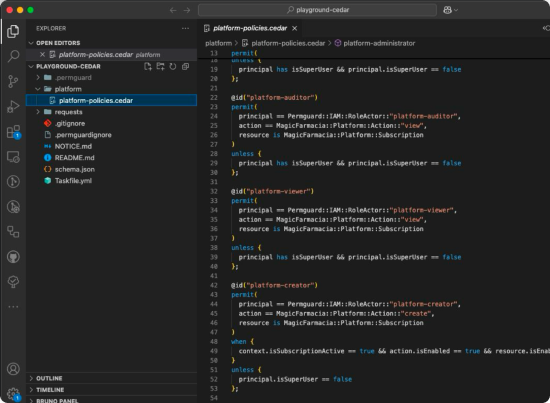

Step: 2
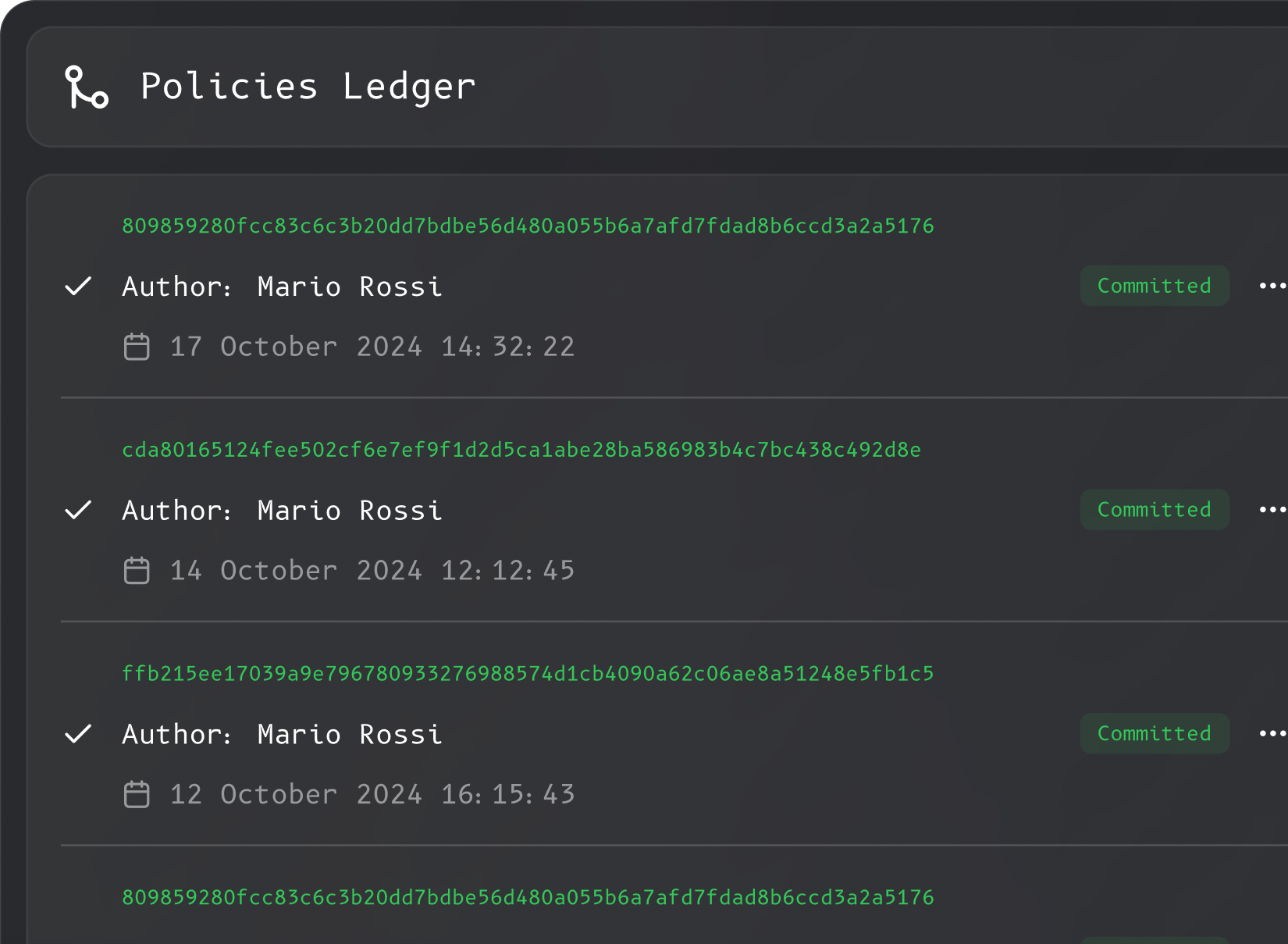


Step: 3


Step: 4